With ssh -i private key filename you can instruct ssh to use an extra private key to try authentication. The documentation is not clear on how to explicitly use only that key. You have an OpenSSH format key and want a PEM format key. It is not intuitive to me, but the suggested way to convert is by changing the password for the key and writing it in a different format at the same time. The command looks like this: ssh-keygen -p -N ' -m pem -f /path/to/key. Navigate to the OpenSSH private key and click Open. Under Actions / Save the generated key, select Save private key. Choose an optional passphrase to protect the private key. Save the private key to the desktop as idrsa.ppk. Supported SSH key formats. Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported. Create an SSH key pair. Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the. The OpenSSH Private Key Format. Traditionally OpenSSH has used the OpenSSL-compatible formats PKCS#1 (for RSA) and SEC1 (for EC) for Private keys. This week I discovered that it now has its own format too, which is the default output format for some installations of ssh-keygen. After peeking at the binary I found, much to my dismay - and very much unlike the ssh public key format (RFC 4253) - that.
OpenSSL is a software library for applications that secure communications over computer networks. This article mentions about precise steps to verify an OpenSSL key against a certificate.
Topic
- How to verify an OpenSSL key against a certificate?
- Verify a SSL key matches a certificate
- Verifying an OpenSSL key matches a certificate
apt
- Linux
Topic
For example we have a certificate file called cert.pem and a key file called key.pem. There are two methods for validation.
- Verify using key and certificate component
- Verify using
MD5 SUMof the certificate and key file
Step 1 – Verify using key and certificate component
Openssl private key contains several modules or a series of numbers. In order to verify the private key matches the certificate check the following two sections in the private key file and public key certificate file. If they match validation is successful.
- Subject Public Key Info: from certificate file
- Private-Key: from key file
To open the certificate and key file execute the following commands.
Example:
Validation:
The modulus in Public Key Algorithm of public certificate matches the modules in Private-Key section of the private key file.
Step 2 – Verify using MD5 SUM of the certificate and key file
Execute the following commands and validate that md5 sum is same for private key and public key certificate file.
Validation:
Output from the above two commands confirms that key matches the certificate.
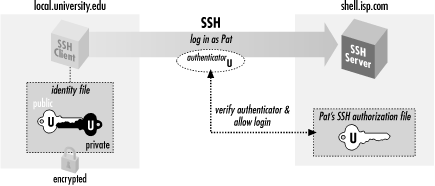
Private keys allow the users to login to SSH without a password. This is considered a safe practice in some cases while also discards the need to remember multiple passwords.
In this tutorial, we would learn how to generate our own SSH Key Pair on our local machine and then configure our Server to use the same for authentication when trying to connect over SSH.
Steps to Login to SSH Without A Password
Let’s go over the process step-by-step to login to SSH without a password. If you’re new, you can start by reading more about how to connect to a remote host using SSH. If you’re ready, let’s get started.
Step 1: Generate SSH Key Pair
On our local machine, we can generate a SSH Key Pair with the following command :
On execution, we are prompted to specify a file in which to save the private key, the default being /home/user/.ssh/id_rsa ; here id_rsa is the name of our Private Key file. You can always specify a different path and name for the Private Key file. For our demonstration, we shall use the default configuration.
Openssh Private Key Extension
Step 2: Provide A Passphrase (Optional)
Next, we are presented with a prompt that asks us for a passphrase that can be used to protect the SSH Private Key from unauthorized access.
However, this field is optional and if left empty, it stores the Private Key file without any protection. In our example, we would leave this field empty. After this, we would have successfully generated our Key Pair. We are also presented with a ‘fingerprint’ and ‘visual fingerprint’ of our key which we need not save.
Step 3: Configure the Server To Use Our Private Key
At this point, we should have the following two files under /home/user/.ssh :
- id_rsa : Our SSH Private Key
- id_rsa.pub : Our SSH Public Key
Openssh Private Key
Take note of the permissions of the private key ( id_rsa ). SSH Private Key files should ALWAYS HAVE 600 PERMISSIONS! If not, change its permission to the said value using the chmod command:
Next, we need to configure our Server to use our private key for login. Now this can be done manually by logging into the Server and configuring stuff manually but there’s a tool ssh-copy-id which does all the hard work for us !
Hence, to configure our Server to use our private key, simply run :
Here,
- USER is the username we want to login as onto the server
- IP is the IP address of our Server
And with that, we can now simply SSH into our Server with :
If you had previously specified a passphrase, you will get a prompt asking for the same :

Note that if you are not using the default path and file names then you need to specify the private key file using the -i flag as follows :
Thus we successfully SSH’d into our machine using our PRIVATE KEY !
Conclusion
Openssh Private Key Format
And with that, we were able to login to SSH without a password on our Linux machine. It’s an easy and more secure way of logging in as it locks you to log in from specific IP addresses. If you’re interested in learning more on Linux topics, continue to follow LinuxForDevices.
